United Nations agency investigates ransomware attack, data theft
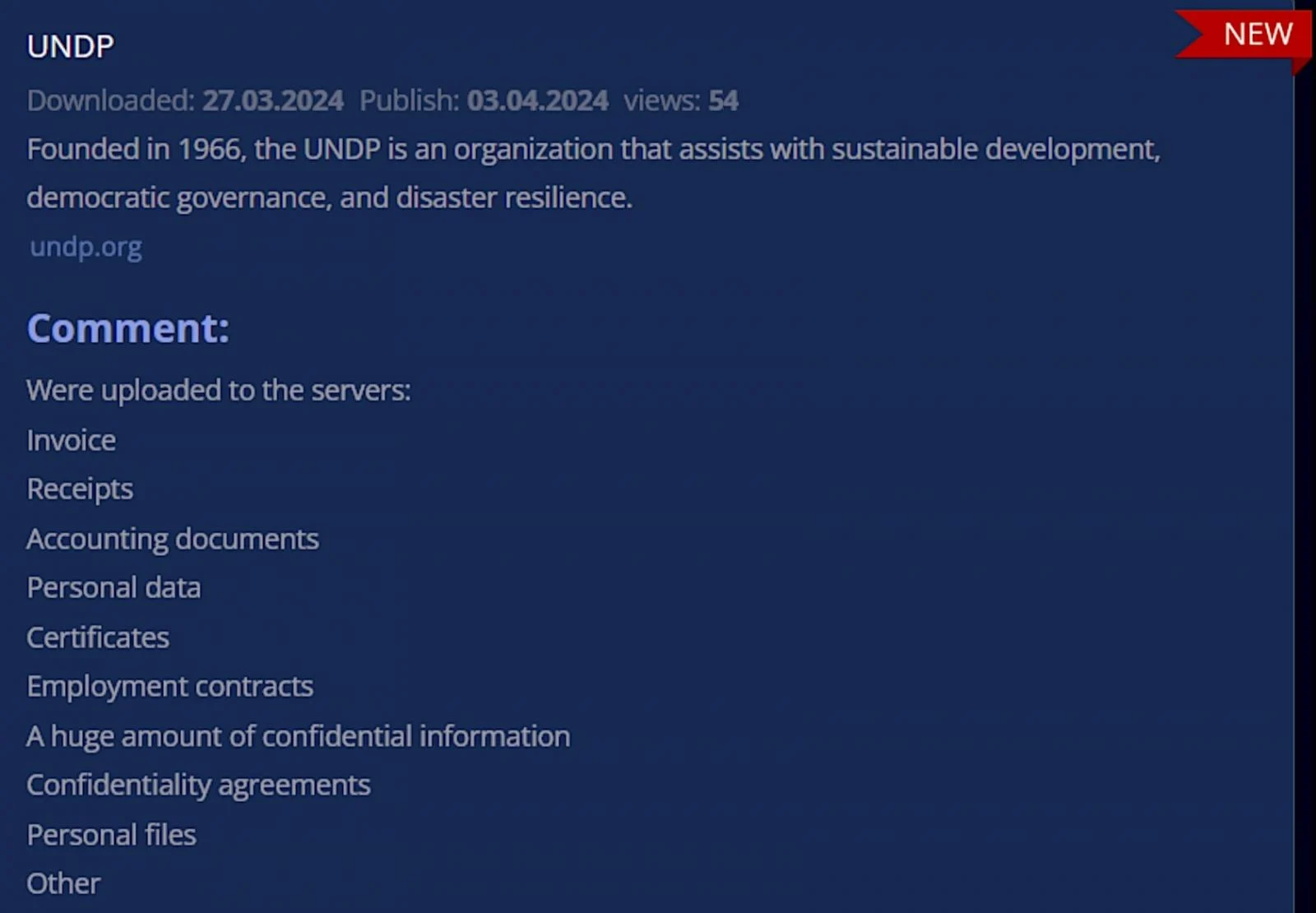
By Sergiu Gatlan, Bleeping Computer The United Nations Development Programme (UNDP) is investigating a cyberattack after threat actors breached its IT systems to steal human resources data. UNDP, the UN's global development network, works in over 170 countries and territories and relies on donations from UN member states and private sector/multilateral organizations to help eradicate poverty and fight inequality and exclusion. In a statement published Tuesday, the organization revealed that the attackers hacked into local IT infrastructure in UN City, Copenhagen, in late March. "On March 27, UNDP received a threat intelligence notification that a data-extortion actor had stolen data which included certain human resources and procurement information," the UN agency disclosed. "Actions were immediately taken to identify a potential source and contain the affected server as well as to determine the specifics of the exposed data and who was impacted." UNDP is now