An Entire Canadian Town Is Being Extorted By Ransomware Cyber Criminals
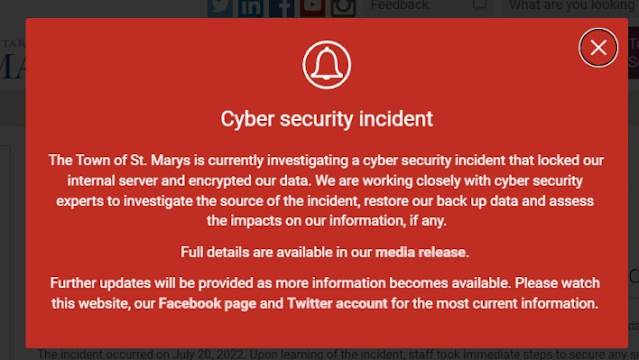
by Lane Babuder, Hot Hardware Ransomware attacks have been on the rise. This time around, the small Ontario, Canada town of St. Marys has been targeted. The ransomware organization behind the attack seems to be LockBit. So far though, no ransom has been paid. The town itself claims that most city functions are still operational and staff are still working and getting paid. Upon visiting the official web site of the town visitors are greeted with a large red box containing the following quote. "The Town of St. Marys is currently investigating a cyber security incident that locked our internal server and encrypted our data. We are working closely with cyber security experts to investigate the source of the incident, restore our back up data, and assess impacts on our information, if any." "We have a skilled and knowledgeable team of Town staff, cyber security experts and legal counsel working around the clock to resolve any issues related to this incident. I have full con