Costa Rica May Be Pawn in Conti Ransomware Group’s Bid to Rebrand, Evade Sanctions
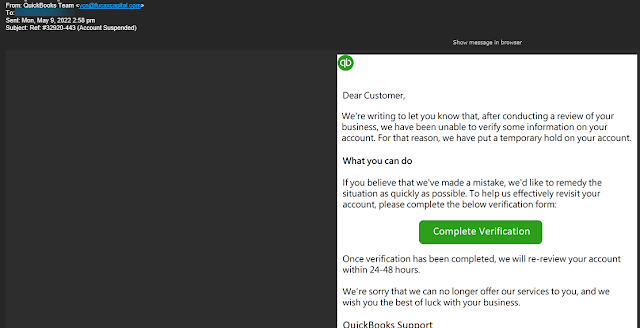
By Krebs On Security Costa Rica’s national health service was hacked sometime earlier this morning by a Russian ransomware group known as Hive . The intrusion comes just weeks after Costa Rican President Rodrigo Chaves declared a state of emergency in response to a data ransom attack from a different Russian ransomware gang — Conti . Ransomware experts say there is good reason to believe the same cybercriminals are behind both attacks, and that Hive has been helping Conti rebrand and evade international sanctions targeting extortion payouts to cybercriminals operating in Russia. The Costa Rican publication CRprensa.com reports that affected systems at the Costa Rican Social Security Fund (CCSS) were taken offline on the morning of May 31, but that the extent of the breach was still unclear. The CCSS is responsible for Costa Rica’s public health sector, and worker and employer contributions are mandated by law. A copy of the ransom note left behind by the intruders and subsequently